Unreachable Mac OS
This article explains how to configure Policy-Based Routing (PBR) on Gaia OS to route traffic according to user-defined policies.
- Unreachable Mac Os Downloads
- Unreachable Mac Os Download
- Unreachable Mac Os X
- Unreachable Mac Os Catalina
Hi, I have installed a new SSD cloned drive and am running MacOS Sierra Which works fine but yesterday it will not connect to WiFi. Everything is normal except it says unreachable when I try to connect. I have booted from my original HDD and everything is working fine. Why won't my cloned SSD. MacBook Pro 13' Unibody Early 2011.
Table of Contents:
- Support for Policy-Based Routing (PBR)
- Configuring Policy-Based Routing (PBR)
- In Clish
- Verifying Policy-Based Routing (PBR) configuration
- Related solutions
(1) Introduction
- How to fix ERRADDRESSUNREACHABLE (Windows, Mac OS, Android, iOS)? Find the best solutions for your case: 'Computer','Mobile device','Nothing else worked','Windows','Mac OS','Android','iOS' For full functionality of this site it is necessary to enable JavaScript.
- Guest Operating System Utility; Windows: VMwareToolboxCmd.exe: Mac OS X: vmware-tools-cli. Because the VMware Tools installer does not modify any PATH environment variables on Mac OS X operating systems, you must type./ before the command. Linux, FreeBSD, Solaris: vmware-toolbox-cmd.
Note: For updated information please refer to sk167135 - Policy-Based Routing and Application-Based Routing in Gaia.
Policy-Based Routing (PBR) lets the user create routing tables that enable Gaia OS to direct traffic to appropriate destinations by defining a policy to filter the traffic based on one or more of the following:
- Interface at which a packet arrives.
- Source IPv4 address and subnet mask.
- Destination IPv4 address and subnet mask.
- Service Port (e.g.: FTP, SSH, Telnet) added starting in R77.30
- Protocol Number (e.g.: TCP, UDP, ICMP) added starting in R77.30
The Policy Rules also specify the action to take if the traffic is matched:
- Prohibit: Send a 'Prohibit' message to the sending host.
- Unreachable: Send an 'Unreachable' message to the sending host.
- Table: Process the traffic according to rules defined in an 'Action Table'
You can define many Policy Rules. Traffic is compared with all the rules in order of the rules' priority - one rule at a time, according to the priority that is configured for the rule.
Policy-Based Routing (PBR) can be used to direct traffic based on where it is coming from (this may include single hosts to entire networks) to where it is going (also single hosts or entire networks). This greatly improves the control that network administrators have in regards to the routing of traffic through a network.
For example, a company may want all traffic from a specific source to use a different route instead of using the default gateway; this can be defined in the action tables for Policy-Based Routing (PBR).
Policy-Based Routing (PBR) static routes have priority over static routes in the OS routing table. When a packet arrives at the OS, the packet is checked for a match to a Policy-Based Routing (PBR) static route:
- If the packet matches, it is then forwarded according to the priority of the Policy-Based Routing (PBR) static route.
- If the packet does not match a Policy-Based Routing (PBR) static route, the packet is then forwarded according to the priority of the static routes in the OS routing table.
Routing and Firewall Processing
It is important to note that routing tables, including PBR tables, are checked after firewall processing is complete.
This means that in situations such as NAT, routing rules are checked against the original source address (refer to sk101562).
(2) Support for Policy-Based Routing (PBR)
| Operating Systems | PBR is supported on the following Gaia OS versions:
|
| Hardware | All Check Point appliances and Open Servers that are supported by the above Gaia OS versions. |
| Clustering | PBR is supported in the following clusters:
PBR must be configured on each of the cluster members individually, and the configuration must be identical. |
| VSX | PBR can be configured only on Virtual Routers in the SmartDashboard. When VSX mode is enabled, Gaia Portal is disabled on Security Gateway as it is not supported in VSX mode, and the Clish command ' Notes:
|
(3) Limitations
- The following features are supported by PBR only starting in R77.30:
- Service Port-based routing
- Protocol-based routing
- The following features are not supported by PBR by default, and are available only as a Request for Enhancement (RFE) via Check Point local office:
- PBR with Source Port routing
- PBR with Ping for reachability detection (available only for R77.20)
- The following features/blades are not supported with PBR:
- IPv6
- URL Filtering
- IPS
- Locally-generated traffic
- Security Servers
- Data Loss Prevention (DLP) blade
- VPN Domain Based
- VPN Route Based (VPN + PBR is supported starting in R80.40 Jumbo Hotfix Take 10 and R81 Jumbo Hotfix Take 2.
- Remote Access VPN
- Anti-Spam blade
- Mail Transfer Agent (MTA) (relevant for Threat Emulation/Threat Extraction/Data Loss Prevention/Anti-Spam blades)
- ISP Redundancy
- The following applications (which use Check Point Active Streaming [CPAS]):
- VoIP (H323, SIP, Skinny, etc.)
- HTTPS Inspection
- HTTP Header Spoofing
- HTTP Proxy
- IMAP in IPS
(4) Configuring Policy-Based Routing (PBR)
Note: For VSX mode, see Section 2 (Support for Policy-Based Routing).
In Gateway mode, Policy Based Routing (PBR) can be configured in Gaia Portal, or in Clish.
The configuration process consists of two parts:
- Configuring the Action Table
- Configuring the PBR Rules
Make sure the following items have been completed before attempting to configure PBR:
- The Security Gateway must be fully configured (including all the relevant Software Blades)
- Policy must be installed on Security Gateway
- Basic routing should be working as expected
Example Scenario:
The following scenario will be used to demonstrate the PBR configuration both in Gaia Portal and in Clish:
Required configuration:
- Traffic from the Remote Office network (192.168.1.0/24) destined for the Home Office network (10.1.0.0/16) should be routed via the MPLS Router at 192.168.128.100
- All other non-local traffic should be sent via the router to the ISP at 192.168.128.74
The diagram below shows the network layout:
(4-A) Configuring Policy-Based Routing (PBR) in Gaia Portal
- Connect to Gaia Portal on Security Gateway with web browser at
https://Gaia_IP_Address Make sure the View Mode displayed in the upper right-hand corner is set to Advanced:
Go to '
Advanced Routing' pane - click on 'Policy Based Routing':The following page opens on the right-hand side:
In the '
Action Table' section, click on 'Add' button:'
Add Policy Table with Static Route' window opens:Parameter Description Table Name The name of the Policy Table. Table ID A numerical ID for the Policy Table. Assigned by the system. Default Route The default static route in the system routing table. Destination The destination of the route. Subnet mask Subnet mask for the destination of the route. Next Hop Type Select one of these:
- Normal: Accept and forward packets.
- Reject: Drop packets and send unreachable messages.
- Black Hole: Drop packets but don't send unreachable messages.
Gateway IP address Next hop gateway IPv4 address. Gateway Interface Security Gateway interface that leads to the next hop gateway. Gateway Priority The preference of the particular route. Range: 1-8. Configure the Policy Table:
Note: The '
Next Hop Type' field is flagged as an error because setting this field to 'Normal' requires at least one entry in the gateway table. We will add the Gateway in the next step.In the '
Add Gateway' section, click on 'Add Gateway' button.Note: You can select either '
IP Address' or 'Network Interfaces'. For the purposes of this example, we will choose 'IP Address'.Configure the Gateway and click on '
OK' button:Check the final Policy Table configuration and click on '
Save' button:In the '
Policy Rules' section, click on 'Add' button:'
Add Policy Rule' window opens:Note: This screenshot is from R77.30
Parameter Description Priority Many Policy Rules can be defined. Traffic is compared to each rule, in order of their priorities, until a match is found or all Policy Rules have been checked. Action The action to take when traffic matches the rule:
- Prohibit - Send a Prohibit message to the sending host.
- Unreachable - Send an Unreachable message to the sending host.
- Table - Perform the actions defined in an Action Table.
Match This section specifies the criteria traffic must match in order for the Policy Rule to apply. One or more of the following may be used; in this case, traffic must match each criteria in order for the system to apply the Policy Rule.
- Interface - The interface on which the traffic was received from the host by the Security Gateway.
- Source, Subnet mask - The IPv4 address and subnet mask of the source.
- Destination, Subnet mask - The IPv4 address and subnet mask of the destination.
- Service port – Enter the service port. Some pre-defined ports are: FTP data (20), Telnet (23), HTTP(80), POP2(109).
- Protocol – Enter the protocol number. Some pre-defined protocols are: ICMP(1), TCP(6), UDP(17).
Configure the Policy Rule and click on '
Save' button:Check the final Policy Based Routing configuration:
- To verify that routing is working as expected, refer to '(5) Verifying Policy-Based Routing (PBR) configuration' section.
(4-B) Configuring Policy-Based Routing (PBR) in Clish
Note: For VSX mode, see section 2 (Support for Policy-Based Routing (PBR) above. To configure a Virtual Router / Virtual System, you must first change the context to that Virtual Device with the 'set virtual-system <VSID>' command.
- Connect to command line on Gaia OS (over SSH, or console).
- Log in to Clish.
Ensure you have the database lock, so you can change Gaia configuration:
HostName> lock database overrideCreate your Action Table:
HostName> set pbr table NAME_of_ACTION_TABLE static-route NETWORK_ADDRESS/MASK_LENGTH nexthop gateway address IP_ADDRESS onBased on our example scenario:
HostName> set pbr table HomeOfficeMLPS static-route 10.1.0.0/16 nexthop gateway address 192.168.128.100 onCreate the Policy Rule:
Based on our example scenario:
Note: If you are using service port or protocol in R77.30 or higher, then example commands are:
Save Gaia configuration:
HostName> save configCheck the final Policy Based Routing configuration:
Based on our example scenario:
- To verify routing is working as expected, refer to '(5) Verifying Policy-Based Routing (PBR) configuration' section.
(4-C) Configuring PBR with 2 ISPs
- Table Name
- Destination
- Subnet Mask
- Next Hop Type
- Add Gateway: IP Address or Network Interfaces
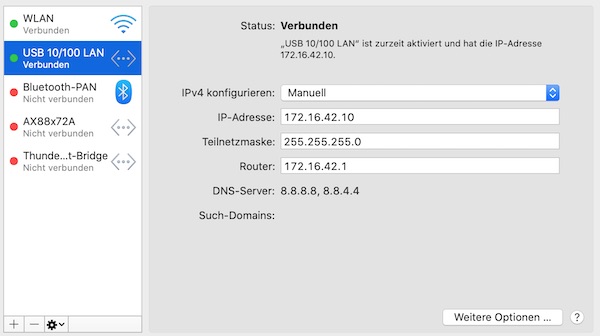
3. Add Policy Rule:
- Priority
- Table
- Interface
- Source IP: x.x.x.x and Subnet Mask: x.x.x.x
- Destination: x.x.x.x and Subnet Mask: x.x.x.x
- Service Port
- Protocol
(5) Verifying Policy-Based Routing (PBR) configuration
Method 1
One method of verifying PBR is configured correctly is to use these commands (in Expert mode):
To list the policy rules:
[Expert@HostName]# ip rule listBased on our example scenario:
Each line is a routing rule, with the priority, matching criteria, and action to take.
The results show us there are four rules for routing traffic.
The second line, with a priority of 1, matches the policy we defined (if we had configured the policy with a priority of 3, it still would have been second in the list, but with a priority of 3).
The action for this rule, 'lookup 1', says traffic matching the specified criteria will be handled according to Action Table with ID 1.To list the action tables:
[Expert@HostName]# ip route list table TABLE_IDBased on our example scenario:
The results show that traffic destined for 10.1.0.0/16 will be routed via 10.10.10.1 out the interface eth1.
Method 2
Another method of verifying that Policy Based Routing is working correctly is to capture the traffic using the '
tcpdump' command.In our example scenario, all traffic destined for the Home Office Network (10.1.0.0/16) should be destined for the MPLS router at 192.168.128.100, and all other traffic should be destined for the ISP router at 192.168.128.74
Since both traffic going to the Internet and traffic going to the Home Office exit via the same interface, we need to use the MAC address of each router to identify them in the tcpdump output.
To obtain the MAC addresses of the routers, enter the following command in Clish:HostName> show arp dynamic allBased on our example scenario:
Display the dynamic ARP entries:
Note: In this example, there has been recent traffic to both the Internet and to the Home Office.
Based on these results:
- Traffic coming to and arriving from the Home Office network should have a Source MAC address or Destination MAC address of 00:0C:29:F3:06:76
- All other traffic should have a Source MAC address or Destination MAC address of 00:0C:29:C9:24:C9
tcpdump' command (in Expert mode) on the relevant interface (eth1) with the '-e' flag.Capture the traffic:
Note: In this example, a host in the Remote Office network is pinging a host in the Home Office.
The first packet in the output is the ICMP Echo Request from the host in the remote network (192.168.1.5), to the host in the Home Office network (10.1.0.1).
The Destination MAC address is 00:0c:29:f3:06:76.
As shown in the output from 'show arp dynamic all' command, this is the MAC address of the MPLS router, which is expected, if the PBR rules are working correctly.
The second packet is the ICMP Echo Response, which has a Source MAC address of 00:0C:29:F3:06:76, indicating it came from the MPLS router, as expected.
(6) Related documentation
- Gaia Administration Guide (R75.40, R75.40VS, R76, R77.X, R80.10).
- Gaia Advanced Routing Administration Guide (R75.40, R75.40VS, R76, R77.X, R80.10)
(7) Related solutions
- sk86187 - Policy Based Routing fails when only default route tables defined
- sk101562 - Policy Based Routing rules matching NATed source address do not work
- sk84480 - Security Gateway on Gaia OS does not send ARP Replies to the directly connected network after adding a Policy-Based Route (PBR) for that network
- This SK replaces sk51564
Не требуется электронная почта, регистрация или установка!
Получите доступ и редактируйте данные и настройки на удаленных компьютерах или серверах с помощью приложения удаленного доступа AnyDesk для Mac. Наслаждайтесь бесшовной связью и простой настройкой. Предложите удаленную поддержку вашим клиентам. Вы можете рассчитывать на совместимость и стабильную работу AnyDesk независимо от того, к какой системе вы подключаетесь, Mac, Windows или Linux.
AnyDesk для Mac устанавливается быстро и просто. Наше приложение удаленного доступа имеет все необходимые функции и инструменты, чтобы из любого места обеспечить стабильное, защищенное и сверхбыстрое соединение с удаленными рабочими столами или серверами. Благодаря гибким лицензиям, AnyDesk можно адаптировать специально под ваши индивидуальные задачи.
Стабильный и защищенный — AnyDesk Remote Desktop для OS X
Высокая частота кадров и незаметная задержка AnyDesk клиента для OS X гарантирует стабильную и сверхбыструю скорость передачи. Собственный кодек DeskRT сжимает и передает изображения без потери качества и обеспечивает практически мгновенный отклик. Даже при интенсивной передаче данных программное обеспечение работает бесперебойно благодаря непревзойденной пропускной способности AnyDesk.
Безопасность AnyDesk для Mac OS — превыше всего! Благодаря стандартной банковской технологии шифрования TLS 1.2 и асимметричного обмена ключами RSA 2048 AnyDesk для Mac OS надежно защищает ваши данные. Корпоративную версию нашего приложения можно легко настроить в собственной сети, чтобы данные никогда не покидали вашу DMZ.
Клиент AnyDesk для OS X без проблем работает на любом компьютере Mac с последней операционной системой Apple или более ранними версиями. Мы постоянно добавляем новые функции.
Маленькое, идеально собранное приложение удаленного доступа AnyDesk для Mac быстро загружается и просто устанавливается. Оно не займет много памяти на вашем рабочем столе или сервере. Установите удаленный доступ к макбуку за несколько секунд!
Переключайтесь между стандартным и расширенным режимом одним кликом: AnyDesk поможет вам сократить функции или перейти к расширенным возможностям
Version 6.1.413 апр. 2021 г.
- Added new CLI commands:
Added CLI commands: Set Password, Register Licence, Get Alias, ID, Status or Version. More info by the link https://support.anydesk.com/Command_Line_Interface
1 мар. 2021 г.
- Support for native resolution:
New option to transfer image in native (Retina) resolution. - Bug on multi-monitor systems:
Mouse pointer coordinate transfer issue on multi-monitor system is fixed. - Bug with rendering:
Bug which may cause image rendering glitches is fixed.
27 янв. 2021 г.
- Extended drag'n'drop support:
Address book supports moving and copying items via drag'n'drop. Create desktop shortcuts for AnyDesk sessions via drag'n'drop - New option for handling display resolution:
'Auto-adapt Resolution' option in Display menu is now supported. - Remote screen handling:
AnyDesk doesn't light up the remote screen when only 'File Manager' feature is used. - Privacy feature support:
Privacy feature availability is now properly reported for older macOS versions. - General usage bugs:
Error which prevented some customers from accessing Address Book is fixed. Error which prevented some customers from accessing Address Book is fixed.
 Version 6.1.0
Version 6.1.012 нояб. 2020 г.
- Support for new macOS:
Added support for new macOS 11 Big Sur. - Support for new hardware:
Added support for new Apple Silicon hardware. - File manager layout bug:
Fixed issue with File Manager UI layut under certain situations. - Fixes:
Fixed couple of small bugs.
7 окт. 2020 г.
- Session recording:
Separated settings for incoming and outgoing automatic session recording. - Security improvement:
Security improved for configurations with AnyDesk service installed. - Remote mouse cursor shape:
Fixed bug when remote mouse cursor has a wrong shape when using specific applications.
22 сент. 2020 г.
- Important - end of support for macOS 10.10 (Yosemite):
Version 6.0.2 is the last to support macOS 10.10 (Yosemite). We strongly recommend upgrading to newer macOS version in order to receive further AnyDesk updates. - Settings improvement:
Improved Settings for Interactive access. - User interface fixes:
Fixed menu actions for File Transfer and VPN sessions. Main window startup position issue fixed. Main window startup position issue fixed. - Screen recording permissions:
Fixed Screen Recording permission detection for Chinese users.
26 авг. 2020 г.
- Improved iOS support:
Support for improved connections to iOS devices. - Speed dial bugfix:
Fixed disabled context menu on Speed Dial items.
6 авг. 2020 г.
- Two-Factor Authentication:
When enabled, an additional dialog will be shown after authentication by password or token, requesting a time-based one-time password provided by a third device. This feature requires an app supporting TOTP.. - Wake-on-Lan:
When enabled, devices running AnyDesk that are currently in sleep mode can be woken up by other AnyDesk devices in the same local network. - Speed dial improvement:
Hide individual item groups in Speed Dial. - Keyboard layout:
Fixed bug when keyboard layout does not match to input into Unattended Access password dialog. - Speed dial bugfix:
Fixed issue which prevented renaming of Speed Dial items. - Incorrect online state:
Fixed issue when sleeping mac reported incorrect online state. - Important - support for macOS 10.10 (Yosemite):
We plan to discontinue macOS 10.10 (Yosemite) support soon. We strongly recommend upgrading to newer macOS version.
17 июл. 2020 г.
- VPN connection:
With this mode two PCs can be put into a private network over a secured connection. - Support for 2FA:
Added support for connecting to Two-factor authentication enabled hosts. - TCP tunnel automated action:
Run user script when TCP tunnel is connected. - Installation procedure:
Drag'n'drop to Applications folder installation method is offered by default now (legacy install method is still supported). - New menu option:
Install Anydesk Service menu option added. - Support for macOS Big Sur beta:
Fixed application crash on macOS Big Sur beta. - Fixes:
Fixed couple of small bugs.
15 июн. 2020 г.
- Bugfix:
Fixed software update notification.
10 июн. 2020 г.
- Address Book view mode:
Thumbnail view mode has been added to Address Book. - Split Full Screen experience:
Split Full Screen experience enabled for Connection Window and Address Book. - Automatic startup:
Option to disable automatic startup of AnyDesk has been added. - Compatibility with mobile devices:
Keyboard input from mobile devices improved. - Connection type icon:
Connection type icon is now displayed correctly. - Fixes:
Fixed couple of small bugs.
7 мая 2020 г.
- Access Control List:
New feature Access Control List (or white list for incoming connections) is now available. - Multiple sessions:
Added support for multiple session windows. - Address Book:
Address Book improved for better usability. - Privacy permissions:
Improved macOS privacy permissions handling. - Compatibility:
Improved compatibility with 3rd party software. - Fixes:
Fixed couple of small bugs.
21 апр. 2020 г.
- Crash bugfix:
Fixed a crash when user account picture is not set.
17 апр. 2020 г.
- TCP Tunnels:
New TCP Tunneling (or Port-Forwrding) feature added. - Address Book new design:
Address Book has been completely redesigned for easier usage. - Start/Stop of session recording:
It is now possible to start/stop recording during the active session. - New information windows:
Added new System Information window and redesigned the About window. - Discovery feature security:
Significantly improved security of Discovery feature. - Accept window security:
Significantly improved security of Accept window. - Power usage improvement:
Optimised power usage for mac laptops. - Improved mouse scrolling:
Mouse scroll sensitivity adjusted. - Remote restart:
Fixed remote restart issue on some configurations. - UI bug fixes:
Fixed Password change UI for unattended access. Fixed Proxy configuration settings UI.
2 апр. 2020 г.
Unreachable Mac Os Downloads
- Error handling:
Improved error handling. - Privacy permissions:
Better macOS privacy permissions handling.
7 февр. 2020 г.
Unreachable Mac Os Download
- Enhanced usability:
Host key option allows users to use Right Command key to control the local macOS while connected to remote device. - Improved compatibility with Android devices:
Added support for Home and Back buttons when connected to Android device. - Installer improvement:
Reduced number of user password requests in AnyDesk installer. - AnyDesk remote update:
Fixed issue when user is not able to reconnect after updating AnyDesk remotely. - Custom Client on Yosemite:
Fixed crash on macOS 10.10 Yosemite related to custom AnyDesk configurations. - Fixes:
Fixed couple of small bugs.
14 янв. 2020 г.
- File manager:
File Manager upload function fixed. - Reconnect after AnyDesk update:
Fixed issue when user unable to reconnect after installing AnyDesk update. - Connection retry attempt:
Fixed crash on multiple connection retry attempt. - Keyboard input:
Improved keyboard input handling. - Fixes:
Fixed couple of small bugs.
11 дек. 2019 г.
- Accept window minimize:
It is now possible to minimize the Accept window into the Dock. - Installation process:
Installation process has been improved. - Recent sessions list:
Fixed display of client name in recent sessions list. - Remove displays:
Fixed indicator of remote displays. - Chat:
Fixed crash on incoming chat message. - Fixes:
Fixed couple of small bugs.
4 дек. 2019 г.
- New Privacy feature:
Enabling privacy mode during a session will turn off the monitor on the remote side so the screen content is hidden. - Blocking user input:
Mouse and keyboard input can now blocked for the computer being controlled. - Automatic screen lock:
New option to automatically lock remote screen when session ended. - Fixes:
Fixed couple of small bugs.
18 нояб. 2019 г.
- Fixes:
Fixed couple of small bugs.
5 нояб. 2019 г.
- Fixes:
Fixed couple of small bugs.
21 окт. 2019 г.
- New features:
Incoming connections are now displayed in the AnyDesk Dock icon - Bugfix:
Fixed issue when user is unable to reconnect to macOS Catalina and Mojave after remote restart. - Fixes:
Fixed couple of small bugs.
10 окт. 2019 г.
Unreachable Mac Os X
- Fixes:
Fixed update function in new version notification and minor bugfixes.
8 окт. 2019 г.
Unreachable Mac Os Catalina
- Fixes:
Fixed crash on macOS 10.15 Catalina for remove keyboard input.
8 окт. 2019 г.
- New features:
Added Discovery feature and better support for macOS 10.15 Catalina - Fixes:
Minor bugfixes
6 июн. 2019 г.
- Redesign:
New user interface design. - Fixes:
Minor bugfixes.
12 окт. 2018 г.
- File manager:
File Manager now available on macOS. - Screenshots:
Screenshots are now stored to the Desktop. - Speed Dial items:
Solved loss of Speed Dial items issue.
13 июл. 2018 г.
- Enhanced Usability:
Implemented custom context menu for AnyDesk ID (claim alias, show alias/show id, copy address). - Claim Alias now available:
Implemented claim alias feature for macOS, users can now choose an alias. - Keyboard Usability:
During a session, the hotkeys of macOS are disabled locally so they can be transmitted to the remote side. - Incoming file manager session refreshes:
Folder content was not refreshed on the remote side on copying files. The file manager view now refreshes automatically. - Compatibility for file manager session:
Incoming file transfer sessions did not allow to change directory to folders containing a space character. - Usability:
Select and Copy using Command+C now works on the AnyDesk ID. - Keep session alive:
AnyDesk now prevents macOS from going to sleep mode when there is an active session. - Request elevation improved:
Fixed an issue in the request elevation feature.
14 июн. 2018 г.
- Fixed Bug:
In some cases, the installation did not work at the first attempt. This should now always succeed on the first entry of the admin password. - Fixed Bug:
The clipoard did not work when connecting to macOS. The clipboard should now work in any case, including clipboard file transfer. Please click the file button at the top of the AnyDesk window in order to receive files from the clipboard on macOS. - Fixed Bug:
Improved stability. - Fixed Bug:
Removed the warning that the file is downloaded from the internet.
11 апр. 2018 г.
- Address Book:
The macOS version now supports your license’s shared address books. - Session recording and playback:
Implemented recording and playback of sessions. - Connect to the login screen:
The macOS version also runs as a service and supports connections to the login screen, full unattended access, and user switching.
Загружая и используя AnyDesk, вы принимаете наше лицензионное соглашение и наше заявление о конфиденциальности.
Обратите внимание наш опрос, чтобы помочь нам сделать AnyDesk еще лучше!
Если загрузка не запускается автоматически, нажмите кнопку «Загрузить» ниже.